Introduction Examples
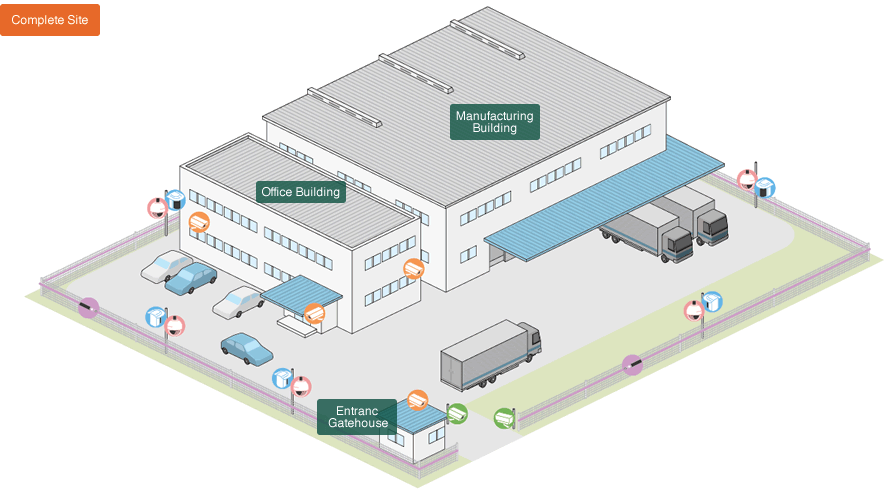
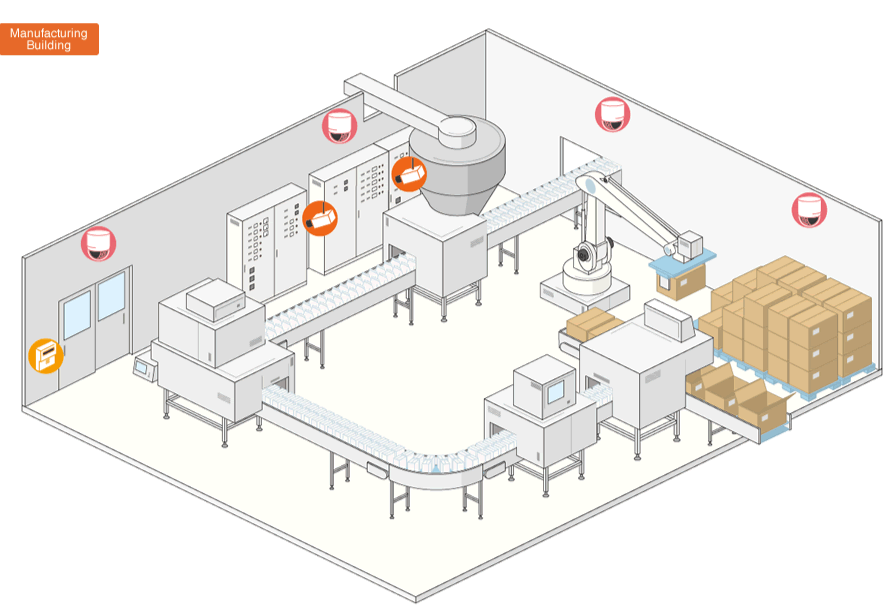
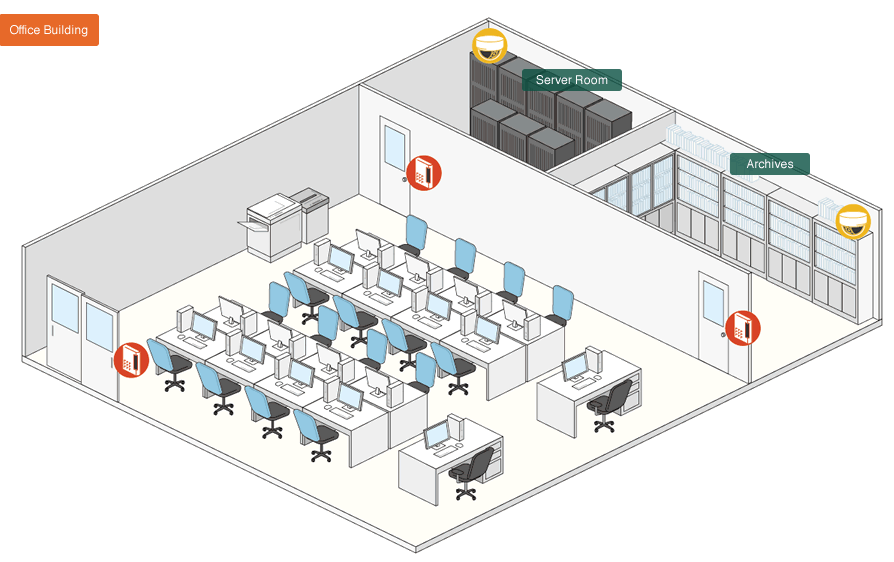
Example for a Factory with our system
Introduction suggestions
This is not just security. It is a system solution to a wide range of issues
Take a look at this example of a factory where our system was installed.
We suggest a security system that features image, authentication and detection functions suitable for each area ranging from the perimeter of the site to the production line. The intention of introducing our system is not only security, but also the safe management of products and a smooth execution of business. For these 3 targets to match the operations of the distribution warehouse, we suggest the distribution facility as target area, provided it is located within the factory premises.
![]()
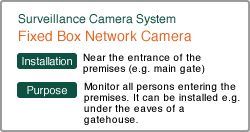
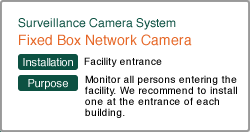
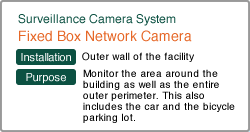




















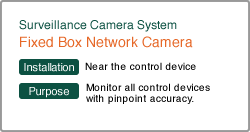
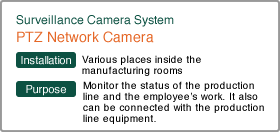









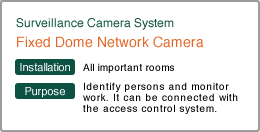





Selecting Introduction Products and Systems
| Perimeter Protection Solution | Perimeter Protection Solution/ Surveillance Camera System |
|||
|---|---|---|---|---|
 |
 |
 |
||
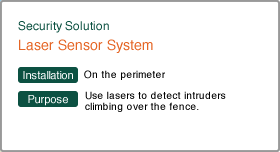
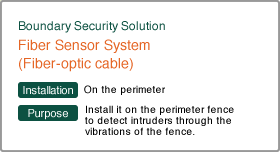
| Laser Security System | Fiber Security System | Network camera | ||
| – | – | SNC-WR632 | ||
| Catch intruders with laser sensors. We have sensors with a detection distance of 60 m, 100 m or 150 m, and for medium to long range. They can easily be installed on large sites. | Fiber optic cables laid on the perimeter fence detect intruders by the vibration of the fence. They can easily be installed on large sites, and have the benefit of a low false alarm rate as well as reduced construction expenses. | The system is connected to the perimeter protection system. It achieves the industry’s top class for a Pan/Tilt speed of max. 700°/sec and a 30x optical zoom which it uses to find every single intruder on the perimeter. | ||
| Surveillance Camera System | |||
|---|---|---|---|
 |
 |
 |
 |
| Network camera | Network camera | Recording software | Storage server |
| SNC-WR630 | SNC-EB630 | RealShot Manager Advanced | EM2210SVX |
| With this camera with its Full HD image quality and industry-leading Pan/Tilt speed of max. 700°/sec as well as a 30x optical zoom you can check the detailed status of the production line equipment and products. | The Full HD high picture quality of this camera allows you to efficiently use the digital zoom function and closely monitor all alarm lamps and numerical values displayed on the control devices. | This software can support up to 32 network cameras. Besides the special camera surveillance screen, the user-friendly GUI has a very convenient integrated map function. | This high-capacity storage for long term recordings is integrated in the server. It can be equipped with up to 30 TB of hard drive space, and RAID configurations for data redundancy. For example, recordings matching food expiry dates, etc. can be stored. |
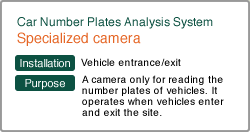
| Vehicle Number Recognition System | Access Control System | |||
|---|---|---|---|---|
 |
 |
 |
||
| Vehicle Vision | Iris authentication apparatus | Non-contact card reader | ||
| – | iCAM7000 | GG-2 | ||
| This system manages the history of all vehicles entering and exiting the factory by reading the vehicle number. It further is possible to change its settings so that VIP vehicles registered as visitors will be noticed immediately. | It can be useful for access control to production buildings where you may not bring any goods with you and therefore IC cards are not allowed either. It prevents spoofing by having iris identification and outstanding accuracy, even compared to other biometric authentication systems. | This card reader is essential to the security of important rooms. It can be connected to OA equipment, such as copiers or shredders, and ask for authentication in order for them to be used, thus contributing to {i>office security<i}. | ||
Criteria for Selecting Introduction Systems
For example, we make sure that each system and each configured device has cleared the special conditions such as the environment around the perimeter of the site, the number of the visitor’s car as target, or the entry method of a locked room where you may not bring any goods with you, and we also ensure that each person concerned has a thorough understanding of the operational methods and rules.
Latest Information & Nature’s Know-How
Security Measures for the Site Perimeter
Even if there is a physical fence, there are practically infinite ways of entering a premise which makes perimeter security extremely difficult. However by combining detection, video, and security systems with people, the ideal “immediate support” is achieved.
Safety Management of Products with Advancing Support
The surveillance camera system for production lines provides you with the material to decide whether the product accident was caused by a system error or a human error, or whatever else occurred in the manufacturing process.