Introduction Examples
Example for a Data Center with our system
Introduction suggestions
The most effective access control on the entire facility
Take a look at this example of a data center where our system was installed.
The most important aspect for security in a data center is thorough access control. Besides providing complete and thorough control, this system implements access rules according to the importance of the area, starting with a security gate after the reception, up to access control with IC card + biometric authentication for server rooms, rooms with air conditioning and electrical equipment, etc.. In addition, each area has a surveillance camera system installed that is connected to the security system.
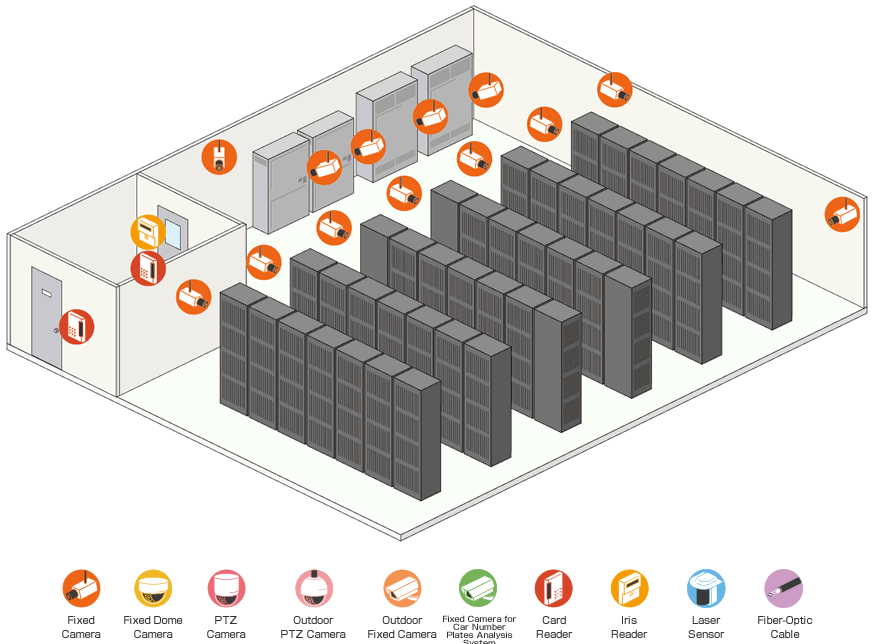
![]()
















Why We Selected This Introduction System
| Access Control System | |||
|---|---|---|---|
 |
 |
 |
|
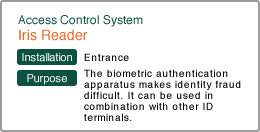
| Card Reader | Card Reader with Touch Panel Scramble Keypad | Iris Reader | |
| GG-2 | GG-2 | iCAMc7000 | |
| This is a basic ID terminal access control system. It controls “who” and “when” people have access with strict rules, and manages the history. | This ID terminal takes security up a notch. It won’t give access if someone only shows a card to identify himself, but requires the corresponding PIN as a double check. | This is a biometric reader for the most important rooms. It prevents spoofing by having iris identification and outstanding accuracy, even compared to other biometric authentication systems. You can make it even safer by using it together with the card reader. | |
| Surveillance Camera System | |||
|---|---|---|---|
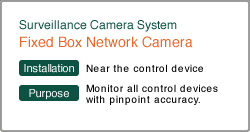
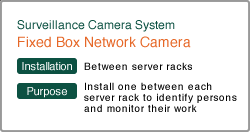
 |
 |
 |
|
| Fixed Network Camera | CMS | Storage Server | |
| NXC-D2002D | iNEX | EM2210SVX | |
| The Full HD resolution of this camera dramatically improves its accuracy of identifying people. It not only enables you to see who is entering the server room, but also to monitor the air conditioning and electronic equipment. | This is a CMS for large scale surveillance camera systems. It is built with a high-capacity storage server, and provides smooth operation with its map function and adjustable recording settings. | This high-capacity storage for long term recordings is integrated in the server. It can be equipped with up to 30 TB of hard drive space, and has RAID configurations providing data redundancy. This storage server fits into the era of Full HD resolution. | |
Why We Chose This Introduction System
This strict access control system takes IC card readers in each area as a basis, and extends this security with biometric readers for the most important rooms. In addition, the access rules (unauthorized access by following someone through the door, two-person rule, etc.) to each area are set according to how high or low the level of security is. Depending on the structure of the facility, we might recommend a flap gate for entering after the reception desk.
Latest Information & Nature’s Know-How
The data center shouldering great responsibility. For a more reliable security system.
It is no exaggeration to say that the data centers currently being utilized across all industries carry a significant social responsibility, together with recent cloud services. Under these circumstances, the installation of a physical security system that controls the access is a more direct and accurate way to prevent troubles and thus avoids problems with people on many sites.